How we protect your account from bad guys, Russians, and robots
We have added some new security features that I think are just so good I have to brag about them. Some of these things are features I have never seen before and it makes me wonder why.
GEO IP WHITELISTING
As you can see, there is a new "IP Filtering" option in the settings menu.
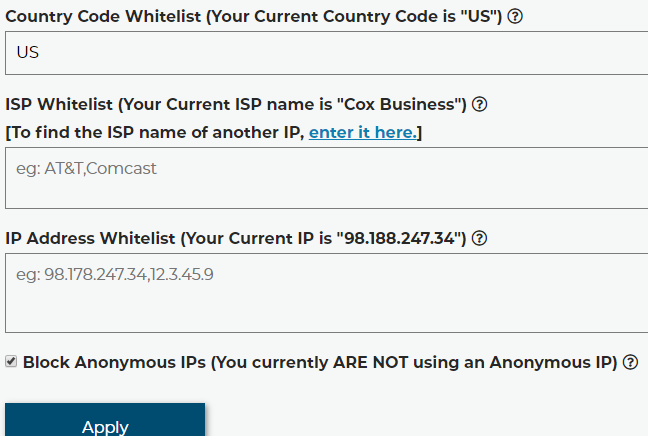
On this page, you will find that you can restrict access to log in by country, Internet Service Provider, and IP address. By default, we are blocking every country except the 7 countries we offer service in. This alone is a huge leap in security, because most cyber-attacks originate from IP addresses located in Russia and Ukraine.
ANONYMIZER DETECTION
At the bottom of that page, notice the "Block Anonymous IPs" option. This will block logins from IP's that are known to be Anonymous proxy servers, Anonymous VPNs, the TOR network, Cloud hosting providers, or any other IP that might be hiding the actual location of the visitor. This helps the Country code whitelist mean something. Without it, a person in a non-whitelist country could still access the site if they were crafty.
How do we know if an IP is Anonymous? We use the maxmind real-time insights service to check each and every login request. It costs us money each and every time someone logs in to get the insight data, and it's among the more expensive APIs we use here, but it's the industry-leading service for this type of information, and only the best will do when it comes to protecting our users.
BREACHED PASSWORDS LOOKUP
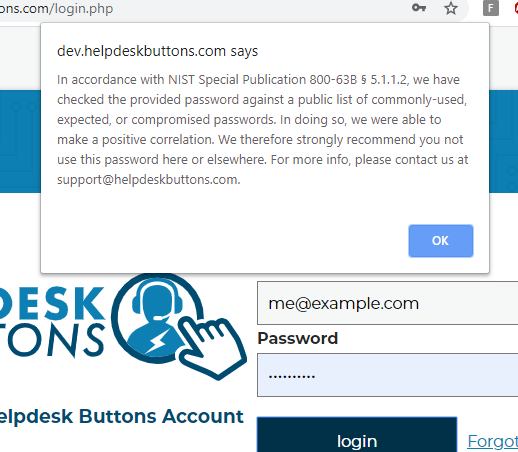
The next piece of really fun infosec I want to show off is something most people won't notice until it matters most.
What you see here is a message that would pop up if you entered an insecure password to login to the site. What is NIST Special Publication 800-63b § 5.1.1.2? Well NIST is the National Institute of Standards and Technology and Special Publication 800-63b are the latest guidelines on digital authentication. There is some interesting stuff in there. For example, did you know that it is considered a poor security practice to require users to change their passwords periodically? Anyway, section 5.1.1.2 says that passwords should be checked against a list of passwords "obtained from previous breach corpuses". There are a lot of those, and we use the haveibeenpwned API to check against all known breach passwords each and every time you log in.
We should be clear, that your password is never transmitted to a 3rd party. Rather we send the first 2.5 bytes of the SHA-1 hash of the password and search the results for the remaining part of the hash.
The result is that if you are using a password that is secure one day, but becomes insecure the next because it was publicized in a breach, we will be able to notify you next time you log in.
This specific feature is a level of preemptive protections that I have never seen in the wild, and I hope to see more companies follow suit.
BOT PROTECTIONS
Another type of protection that is much more recognisable but deserves mention is reCaptcha. reCaptcha is all over the web, and for good reason, it works. Most sites are using it for things like stopping forum spam, but it prevents other malicious bots and brute-force password attacks extremely well. Something that users of our site probably have not noticed though is that we use reCaptcha all over the place and you never see it.
This is because reCaptcha offers an invisible option, which stays completely out of the way unless there is reasonable suspicion that the user might not be human, then it springs into action asking you to click stop signs and traffic lights. The only sign that it is there protecting your account is this little symbol at the bottom right of the page.
Look for it next time you log in. Keep and eye out for it on pages other than the login page. It's a little thing that makes a big difference.
OUR PAST ACHIEVEMENTS
The above items are just our newest security features. If you missed the older blog posts, we also have a very powerful yet simple heuristic-based suspicious activity blocking agent, and anti-malware upload scanner, as well as a very sophisticated cryptography-based open source utility we call "the gatekeeper" which is responsible for keeping private data private.
OUR GENERAL APPROACH
Probably the most important security feature we have though is our attitude toward security. The general idea here is that everything takes a back seat to security, and it's really that mindset that matters most I think.
One good example of this is our approach to security patches on our servers. Most of the critical infrastructure here is "serverless" in that it runs on AWS Lambda. But the servers we do have run Ubuntu Server edition. Ubuntu has support for automatic security patches but it's off by default. If you enable it, then it will install security patches and email you, but will require manual intervention to reboot the server to complete the install (if a reboot is required, which it usually is not). Furthermore, it will run into a roadblock on upgrades that would overwrite config files that have been edited since they were installed. Should it overwrite your work to force this update to install? The default it just to ask what to do.
There are tons of opinions online that the auto-update feature should not be enabled in the first place, that it is bound to break things and cause downtime. There are plenty of admins (most?) that think unexpected downtime at odd hours is the worst thing that can happen. Windows sysadmins like to point to WSUS as the gold standard. "Always test your patches thoroughly before deployment". The problem is that people get sick, or busy, or complacent, and patches don't get tested for weeks.
Those admins are wrong, unexpected downtime is not the worst thing that can happen, unexpected security breaches are. If we have to go in and fix something that broke from a security patch, then so be it. It's the price we pay for secure servers.
We have configured all or our servers to reboot immediately on security update without warning and overwrite any needed config files to install the update at all costs. They check for new security updates hourly.
Chris Wheeler, CTO, HelpdeskButtons